Application Threat
Modeling
Helping Clients Learn & Build Risk-Based Threat Models
PASTA as a threat model framework is adopted and used by worldwide organizations.
Allow us to tailor a PASTA application threat model for your application so you can effectively apply the risk-centric methodology within the regiment of their software security assurance process.

As a company focused on simulating realistic attack patterns, Inspium doesn’t negate the physical possibilities of intrusion. Offering both traditional red teaming exercises and a new variant called Organizational Threat Modeling exercises, we took traditional red teaming and leveraged the PASTA threat modeling framework to deliver attack simulations against organizations who wish to know the resiliency of their company from all angles. Whether you have a targeted need that is best served by a traditional red team, or would like a cyberthreat exercise that simulates the likely threat motives and underlying attack patterns against employees, vendors, physical locations, self-managed logical networks, and Cloud based services. More detail around both services is presented below.
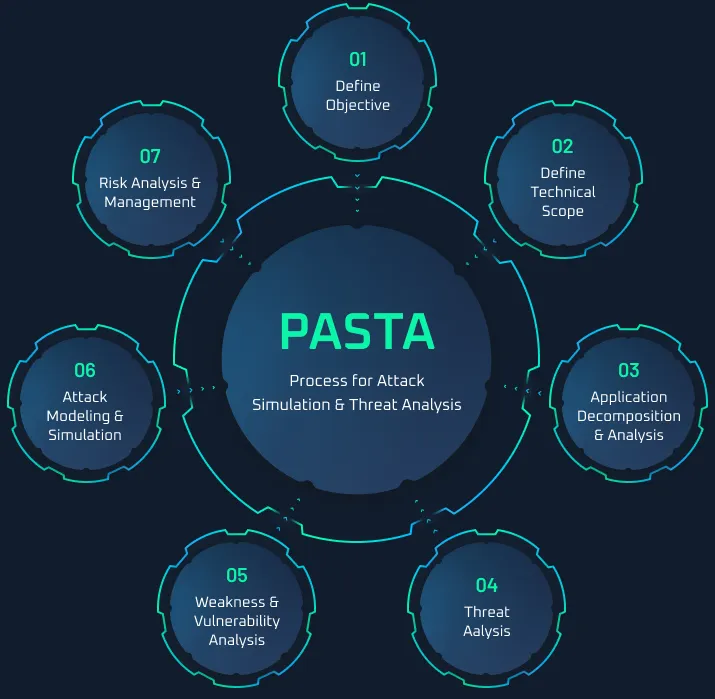
PASTA Threat Modeling (Process for Attack Simulation and Threat Analysis) Inspium’s Risk-Based Threat Model Methodology
Inspium leverages our PASTA (Process for Attack Simulation and Threat Analysis) methodology to apply a risk-based approach to threat modeling. This methodology integrates business impact, inherent application risk, trust boundaries amongst application components, correlated threats, and attack patterns that exploit identified weaknesses from the threat modeling exercises. Prior to the PASTA threat model, most application threat models were not even considering actual threats. As the name implies, a key goal for threat modeling is to do just that – model threats. Threat categorization mnemonics (like STRIDE) are helpful for beginners, but product managers and their superiors are eager to know which threats are topical to their business, product, and platform. Furthermore, limiting threats to a handful of categories may not include the actual threats adversarial groups are planning. PASTA provides a risk centric threat modeling approach that is evidence-based. Inspium's security experts correlate real threats to your attack surface of application components and identify risk by first understanding the context of what the software or application is intended to do for the business or its clients. We also conduct exploitation tests that support threat motives within the model to validate whether they are probabilistic. Correlating viability with sustained impact allows this methodology to resonate as a highly effective risk-focused threat modeling approach.